Building Trust through Transparent Engineering: A Journey to Enterprise Readiness
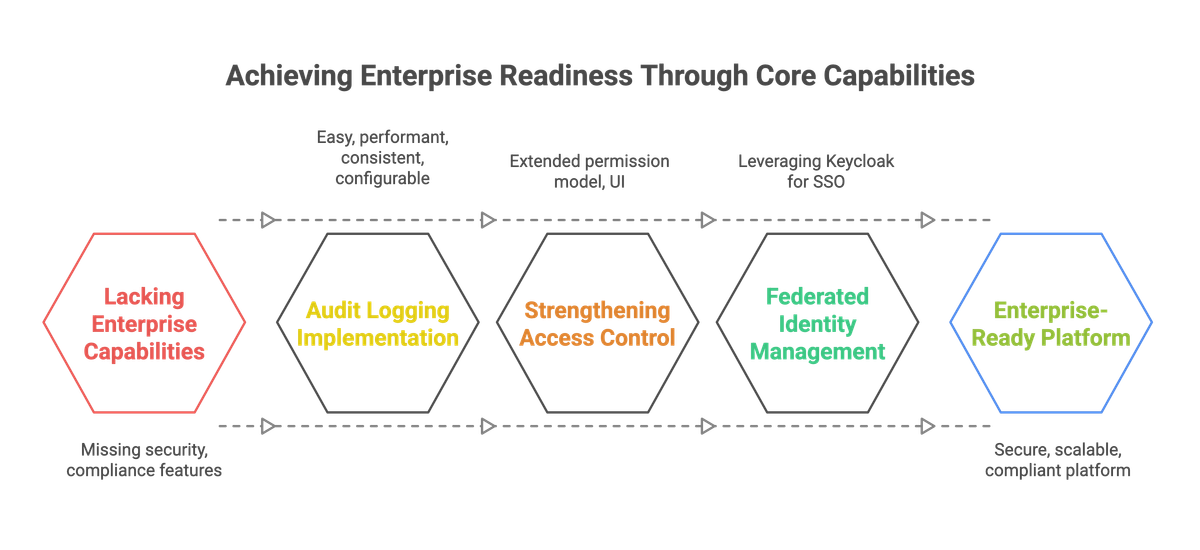
Enterprise customers demand more than just functionality—they expect platforms that meet the highest standards of security, scalability, and compliance. While working with the engineering team at an automation startup, we were at a critical juncture. The product was gaining traction across industries, automating processes in healthcare, finance, and logistics, but lacked core capabilities essential for operating in regulated, security-conscious environments.
Audit logging, fine-grained role-based access control (RBAC), and federated identity management with Single Sign-On (SSO) and Multi-Factor Authentication (MFA) were either missing or handled in piecemeal ways. Without these, we risked not only customer dissatisfaction but failing key compliance benchmarks like SOC2 Type II and enterprise infosec reviews. Prospective clients had security checklists that we couldn’t yet complete. We needed to solve this comprehensively, quickly, and without ballooning the cost.
This is the story of how we made our platform enterprise-ready—strategically, scalably, and with a developer-first mindset.
Recognizing What Was at Stake
The product was functionally rich but operationally opaque. We had multiple external and internal integrations—REST APIs, file stores, email systems, external databases, even FTP and SSH endpoints—all handling automation workflows and sensitive operational data.
We couldn’t answer simple but vital questions:
- Who triggered which automation and when?
- What data was sent or received across third-party systems?
- Were sensitive configurations or integrations ever modified?
Our customer base was growing rapidly, but enterprise clients consistently asked about audit logs, SSO compatibility, and RBAC enforcement. The gaps were costing us deals. It wasn’t just a feature request; it was a gatekeeper to higher-value clients. At the same time, we had to be frugal. We didn’t have the luxury of throwing money or time at the problem. Every engineering hour had to count.
Designing for Auditability Without Slowing Down the Team
We began with audit logging. Our first challenge was alignment: teams were under pressure to deliver automation connectors, integrations, and dashboard improvements. Adding logging across every system felt like an extra burden. To succeed, the solution had to be:
- Easy to use (zero resistance from developers)
- Performant (low overhead during execution)
- Consistent (uniform logs across modules)
- Configurable (supports dynamic log destinations and redactions)
We considered several approaches:
- Manual Logging at every sensitive operation. This would require discipline across teams and constant code reviews to catch gaps. It didn’t scale.
- Middleware / Service Wrappers, where all integration calls went through a proxy layer. Clean architecture-wise, but would require refactoring hundreds of files.
- Aspect-Oriented Programming (AOP) using Spring and annotations. Promising, but we weren’t sure if teams would adopt it.
We tested the third option. I created a prototype with a custom @Audit annotation using Spring AOP and Log4j. This module captured the method name, parameters, user identity, execution time, source IP, and outcome. Logs were structured in JSON and pushed to a secure audit stream configured via Logstash. We ensured logs were signed using SHA-256 checksums before transmission to ensure tamper evidence.
One technical hurdle was ensuring asynchronous logging didn’t impact the performance of real-time automation execution. We introduced a bounded queue and non-blocking appenders to ensure low-latency writes and prevent slowdowns during spikes.
The breakthrough came when we made it dead simple: annotate a method with @Audit, and it just worked. No other changes needed. Teams embraced it. Within two weeks, we had >80% coverage on all critical paths. The remaining 20% followed after we set a CI rule that flagged unaudited actions during PR reviews.
This solution was frugal (built in-house, reused existing frameworks), scalable, and developer-friendly. We didn’t sacrifice speed—we enhanced it.
Strengthening Access Control Without Breaking Existing Workflows
Our RBAC story was equally constrained. We had a flat role system: admin or user. It wasn’t enough. Enterprise clients wanted role separation (viewer, editor, admin), action-scoped permissions, and tenant-specific overrides.
Rather than rewriting the permission model entirely, we extended it:
- Created a permission schema in our PostgreSQL database, mapping roles to granular actions
- Introduced permission inheritance, allowing admin roles to include editor and viewer scopes
- Used Spring Security’s
@PreAuthorizewith SpEL expressions to check dynamic permissions - Added helper functions for evaluating contextual access (e.g., "can this user export this file?")
One technical challenge was managing the permission explosion as tenants created more roles. We designed a normalized structure for role-action-resource mapping, optimized with indexed lookups and batched permission evaluation during login token issuance.
We introduced a UI under admin settings for role creation and mapping, allowing customers to define custom roles without needing to contact support. For testing, we added a "permission simulator" that allows admins to see which actions a user would be allowed to perform based on current role mappings.
This also became an opportunity to empower customers. By giving them tools to manage access internally, we reduced support overhead and increased stickiness. One client told us, “This feels like we’re in control. We don’t have to wait 2 days to onboard a new team.”
Making Identity Management Effortless with Keycloak
The biggest challenge came with federated identity. Customers wanted us to integrate with Okta, Azure B2C, Google Auth, and even on-prem LDAP. Each implementation required different flows (OIDC, SAML, or custom headers), and our team didn’t have identity experts.
We looked into:
- Building individual adapters (time-consuming and hard to test)
- Using Auth0 (great solution, but expensive as the user count grows)
- Leveraging open-source Keycloak as an identity broker
We chose Keycloak.
Configuring Keycloak was non-trivial. The default configuration interface was dense and unapproachable for customers. We reverse-engineered Keycloak’s admin REST API and created a middle-layer service to abstract realm and client setup. This API allowed multi-tenant configuration through our own frontend without exposing the complexity of Keycloak's native admin console.
We created Terraform scripts and Docker Compose templates to manage realms, clients, scopes, and MFA policies. We provisioned Keycloak to run in HA mode using PostgreSQL as a shared state backend, integrated with our secrets manager for key storage, and placed it behind a load-balanced ingress with enforced TLS.
Keycloak token payloads were customized to include our internal user identifiers, feature flags, and customer tier metadata. We also developed a plugin to auto-sync user role changes with our database in near-real-time.
Within 6 weeks:
- We supported SSO with Okta, Azure, Google, and LDAP
- MFA could be toggled at the tenant level, with TOTP and push notification options
- Token-based authorization worked end-to-end with dynamic claims evaluation
This earned deep trust with security teams. During a client demo, the CISO said, “You’ve thought of things we hadn’t. This gives us confidence to deploy to all departments.”
Speed vs Quality vs Cost: Finding the Right Balance
At every step, we faced trade-offs:
- Should we buy vs build?
- Should we delay a feature for security?
- Should we optimize for MVP or long-term scalability?
We stayed frugal. We avoided expensive third-party identity solutions by mastering Keycloak. We didn’t buy an audit log SaaS—we reused our ELK stack with some improvements. We chose solutions that required upfront thinking but little downstream maintenance.
We also slowed down in the right places. Instead of rushing RBAC in two sprints, we took four but ended with a flexible policy engine. That saved us countless hours when onboarding new customers with different needs. We prioritized long-term correctness over short-term delivery.
Being "right almost all the time" meant:
- Writing internal RFCs before changing access control models
- Creating data migration scripts with rollback support for role schemas
- Running tabletop exercises to simulate audit events, identity outages, and misconfiguration scenarios
- Maintaining strict test coverage and static code analysis gates for all security-related modules
We conducted chaos testing on Keycloak by rotating signing keys, expiring tokens mid-session, and disabling MFA during login to see if our downstream systems handled failures gracefully.
These steps took time, but they minimized regret. We didn’t just meet the bar—we raised it.
The Results
- Audit Coverage: 98% of sensitive actions were audited within a month; audit logs retained for 1 year with tamper-proof archiving
- RBAC: Role granularity improved adoption across security-conscious teams; time to provision a new role dropped from 3 days to under 30 minutes
- SSO: 5 major enterprise identity systems supported; new tenant onboarding reduced from 10 days to 2 hours
- MFA: Enabled on 100% of customer logins within 3 months, enforced via policy at the tenant level
- Trust: Feature reviews with client security teams became showcases, not defenses; multiple clients cited identity and access architecture as key reasons for choosing our platform
Final Reflections
Enterprise readiness isn’t a phase—it’s a mindset. We built logging, access control, and identity from first principles, but with empathy for the customer and humility as a team.
We empowered developers with tools that made compliance simple. We empowered customers with controls that built trust. We made deliberate, frugal decisions that scaled.
Today, our platform isn’t just a product—it’s a trusted part of our customers' operational stack.
If you're modernizing a startup platform for enterprise scale, start with the fundamentals: visibility, identity, and control. From there, trust follows.