STRIDE Threat Model in the Secure Development Lifecycle: A Practical Guide
The Problem with Insecure Software
In a world driven by software, security breaches have become alarmingly frequent. From healthcare to finance, organizations are grappling with data breaches, system compromises, and reputational damage. Most of these threats don’t stem from zero-day vulnerabilities but from overlooked design flaws and insecure development practices.
Despite widespread awareness, many teams treat security as an afterthought. Security often enters the picture only during final testing or post-deployment patches. This reactive approach leads to increased costs, regulatory non-compliance, and exploitable software.
The Need for Proactive Threat Modeling
To address security early in the software development lifecycle (SDLC), teams need structured methodologies to anticipate and mitigate risks. One of the most effective models for this is STRIDE — a threat classification framework developed by Microsoft. When incorporated into a Secure Software Development Lifecycle (SSDLC), STRIDE helps identify potential security threats before a single line of code is written.
What is STRIDE?
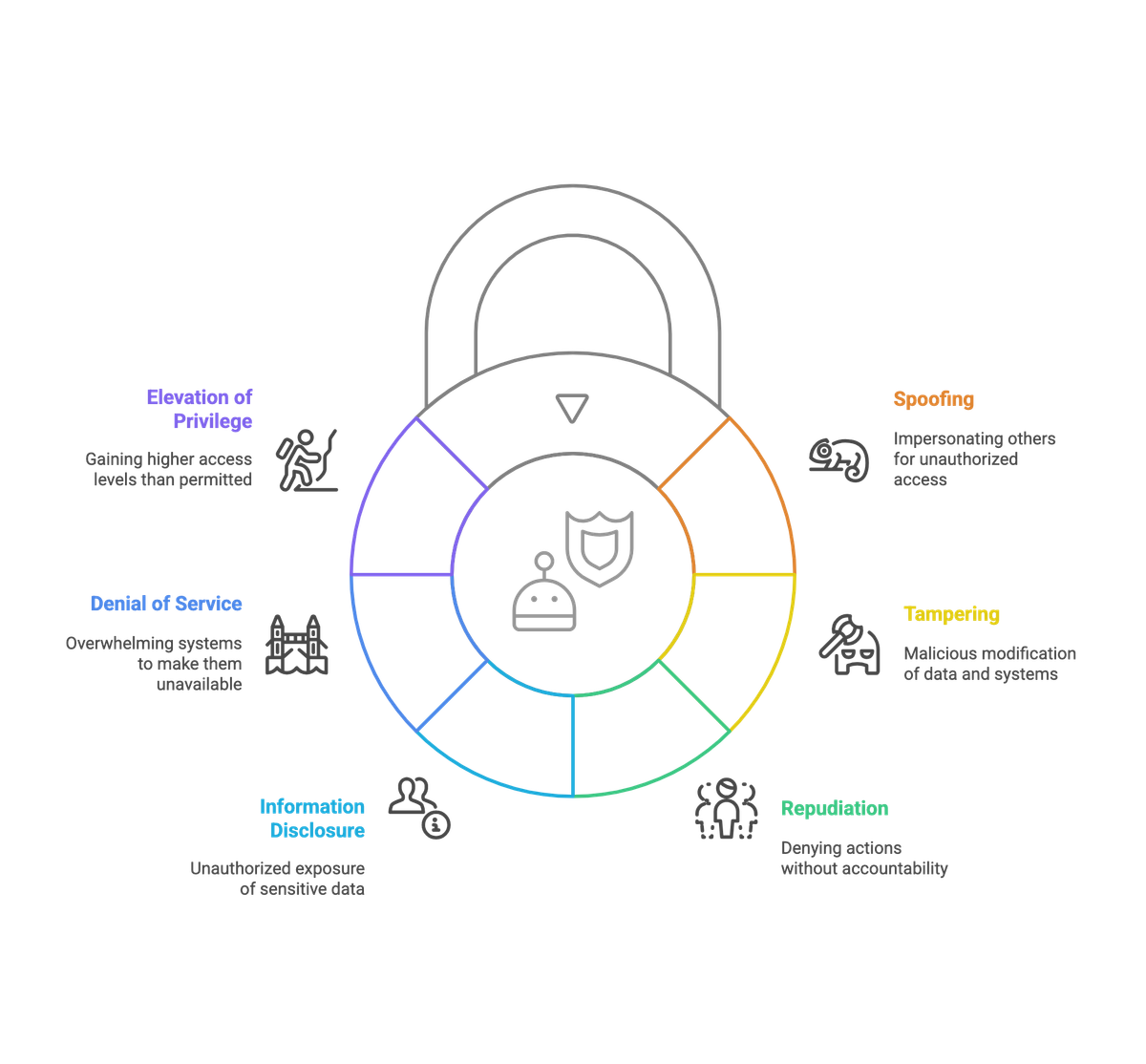
STRIDE is a mnemonic for six categories of threats:
| Threat | Description | Real-World Examples | Mitigation Strategy |
|---|---|---|---|
| Spoofing (Identity) | Impersonation of a user or system by faking credentials, tokens, or certificates. Undermines authentication mechanisms. |
Storm-0558 Cloud Breach (2023) – Stolen signing key to forge tokens. DigiNotar CA Breach (2011) – Fraudulent SSL certificates. |
Enforce MFA and mutual TLS Use certificate pinning and short-lived tokens Apply NIST IA-2 controls, Zero Trust IAM Scan secrets in CI/CD, use secure vaults |
| Tampering (Integrity) | Unauthorized modification of code, files, configurations, or traffic. Includes supply chain and parameter injection attacks. |
SolarWinds Orion Attack (2020) – Supply chain compromise. CCleaner Malware Update (2017) – Code tampering in updates. |
Secure CI/CD pipeline and sign artifacts Use checksums and hash verification Follow NIST SI-7, CIS Controls 2 & 5 Use file integrity monitoring tools like Tripwire |
| Repudiation (Non-repudiation) | Actions cannot be traced or attributed. Lack of secure logs allows attackers to deny malicious activities. |
Bangladesh Bank Heist (2016) – SWIFT logs altered. Yahoo Breach (2013–2016) – Undetected due to poor logging. |
Use centralized, immutable audit logs Digitally sign sensitive events Apply NIST AU controls, CIS Control 8 Deploy SIEM tools and tamper-evident logging |
| Information Disclosure (Confidentiality) | Exposure of sensitive data via misconfigurations, vulnerabilities, or insecure transport/storage. |
Equifax Breach (2017) – Failure to patch Apache Struts. Capital One AWS Leak (2019) – S3 and WAF misconfig. |
Use TLS 1.3 and AES-256 Apply least privilege and tokenization Scan cloud/IaC configurations for public access Follow NIST SC controls and OWASP data protection best practices |
| Denial of Service (Availability) | Flooding or resource exhaustion that renders services unusable. Includes DDoS and logic bombs. |
Dyn DNS DDoS (2016) – Mirai botnet attack. GitHub DDoS (2018) – Memcached-based 1.35 Tbps attack. |
Deploy DDoS protection (Cloudflare, AWS Shield) Use rate limiting, CAPTCHAs, circuit breakers Auto-scale infrastructure, test with chaos engineering Apply NIST SC-5, model abuse cases (Microsoft SDL) |
| Elevation of Privilege (EoP) | Gaining unauthorized admin-level access. Often through bugs, misconfigurations, or weak access controls. |
ZeroLogon Vulnerability (2020) – Escalation to domain admin. Dirty COW Linux Exploit (2016) – Kernel race condition used for root access. |
Apply least privilege and RBAC Use static/dynamic analysis for EoP bugs Implement PAM, kernel hardening (AppArmor/SELinux) NIST AC-6, OWASP ASVS/MASVS authorization checks |
Each STRIDE threat maps directly to fundamental security goals:
- Spoofing affects Authentication
- Tampering affects Integrity
- Repudiation affects Non-repudiation
- Information Disclosure affects Confidentiality
- Denial of Service affects Availability
- Elevation of Privilege affects Authorization
These threat categories help security teams systematically identify vulnerabilities across components, services, and interfaces, ensuring that potential risks are flagged and mitigated early in the design process.
STRIDE in the Secure Development Lifecycle (SDLC)
Integrating STRIDE into each SDLC phase ensures that threats are proactively identified and mitigated:
| SDLC Phase | STRIDE Integration | Techniques & Tools |
| Requirements | Define security and privacy requirements using STRIDE categories | Use compliance checklists (e.g., ISO 27001 Annex A), privacy impact assessments |
| Design | Create threat models for architecture, identify threats for each component | Microsoft Threat Modeling Tool, OWASP Threat Dragon, IriusRisk |
| Implementation | Adopt secure coding practices to address identified threats | Static code analysis (e.g., SonarQube), secure coding guidelines (OWASP) |
| Verification | Test for presence of STRIDE threats using automated and manual tests | Penetration testing, SAST/DAST, security unit tests, fuzzing |
| Release | Final security review to confirm all threats are mitigated and documented | Security checklists, compliance audit readiness (HIPAA, GDPR, SOC2) |
| Maintenance | Continuous monitoring for new threats; patch STRIDE vulnerabilities quickly | Threat intelligence, SIEM tools, incident response plans |
Conclusion: Secure by Design with STRIDE
Security isn’t something to tack on at the end. STRIDE offers a practical, structured approach to integrating threat identification throughout the SDLC. By proactively addressing Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege, teams reduce risk, lower remediation costs, and improve compliance.
Adopting STRIDE with tools like Microsoft TMT and aligning with standards like ISO 27001 and HIPAA creates not just secure products, but secure organizations. STRIDE isn’t just a model — it’s a mindset.